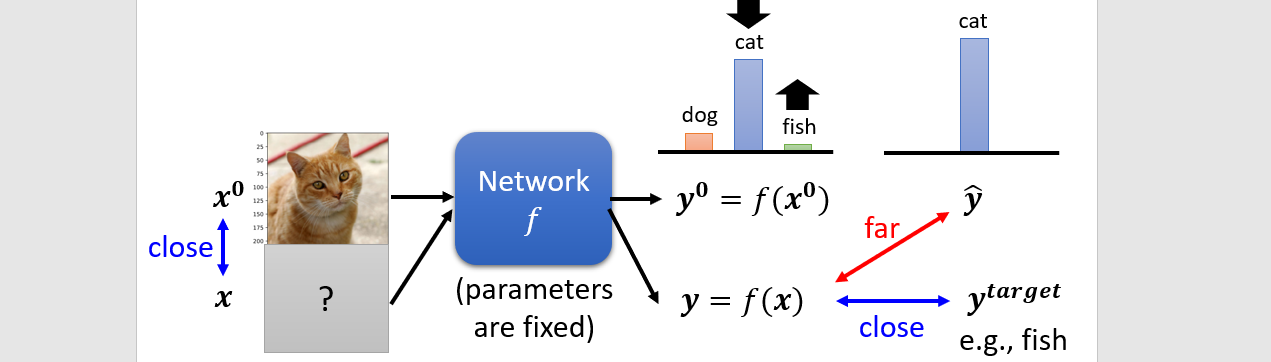
Adversarial attack
Small noisy is added to the input - 以假亂真
- Benign: original input
- Non-targeted: attacked output far from the correct output
- Targeted: attacked output close to the target

Attack
Defense
- Passive defense
Filter out noise
- Blur, smooth, compression
- Generator
- Randomization(resize, padding, selection)
- Proactive
Adversarial training
Find adversarial input , train with &
Data augmentation
Adversarial training for free → without additional computation